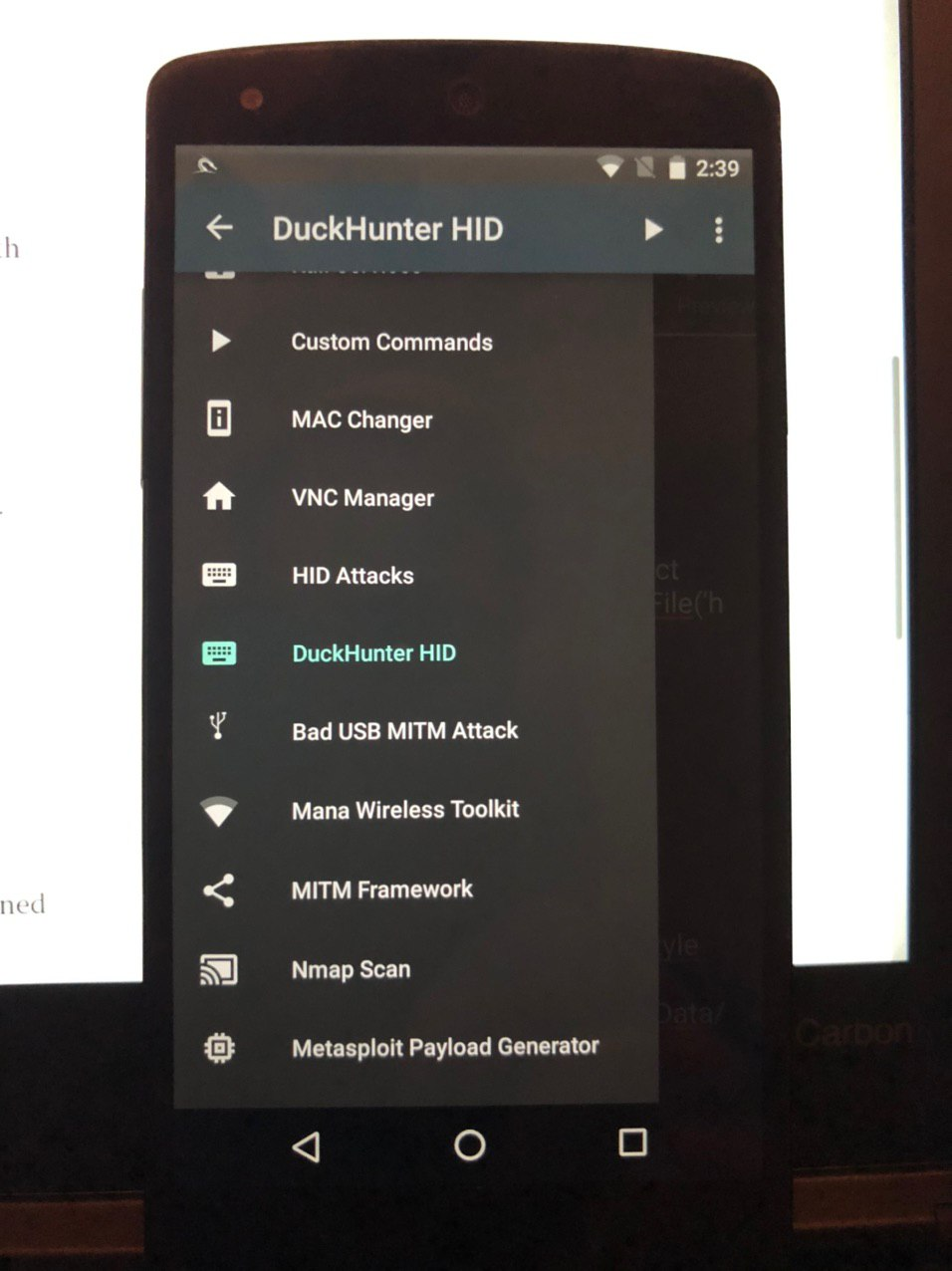
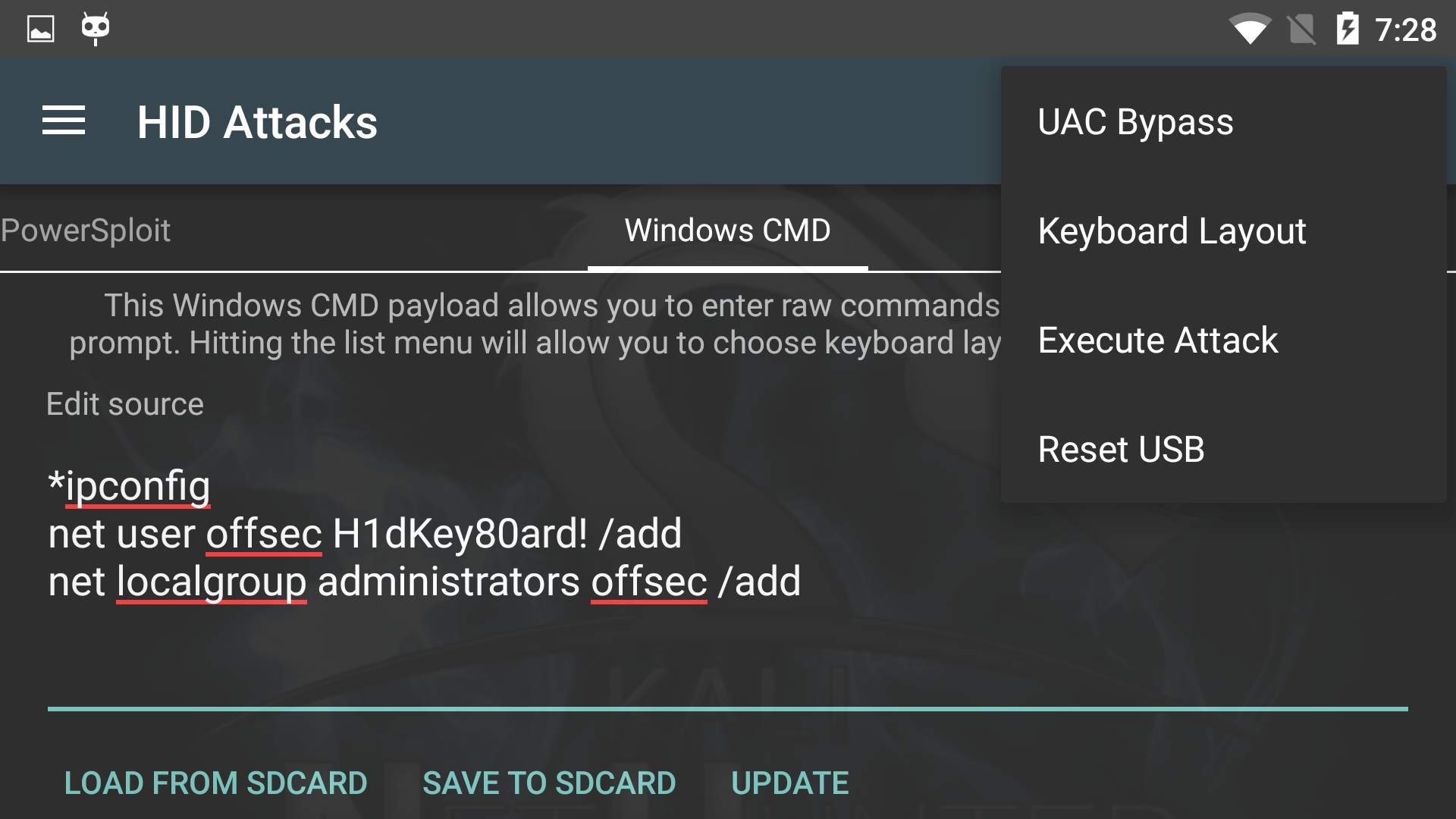
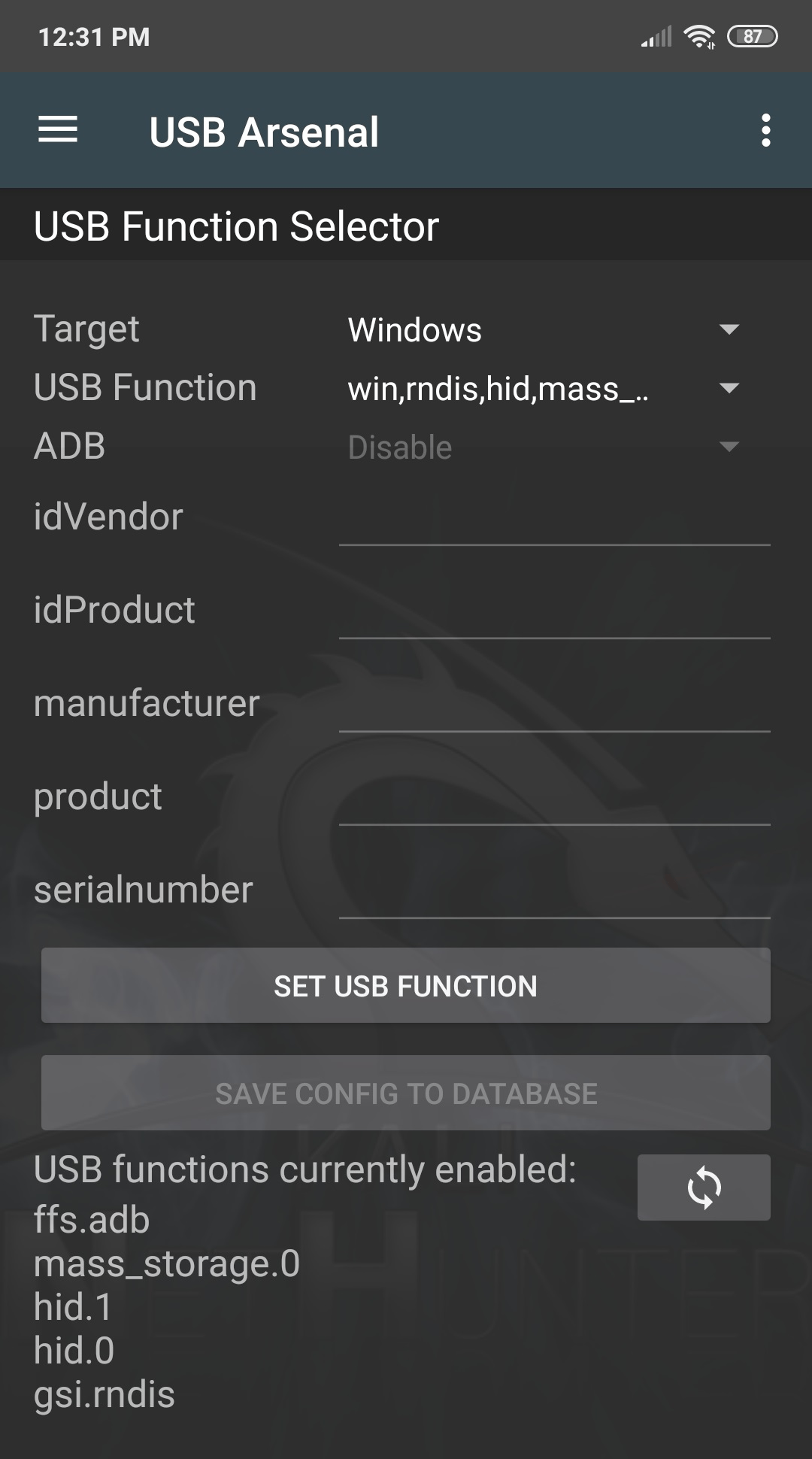
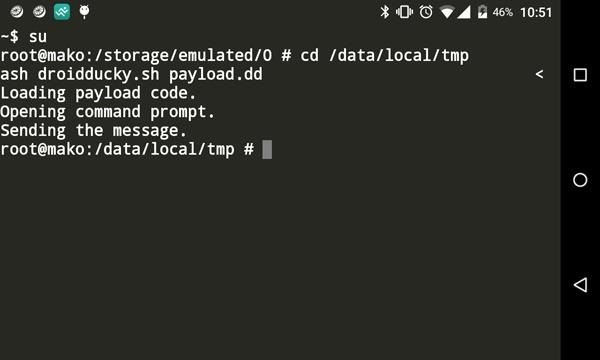
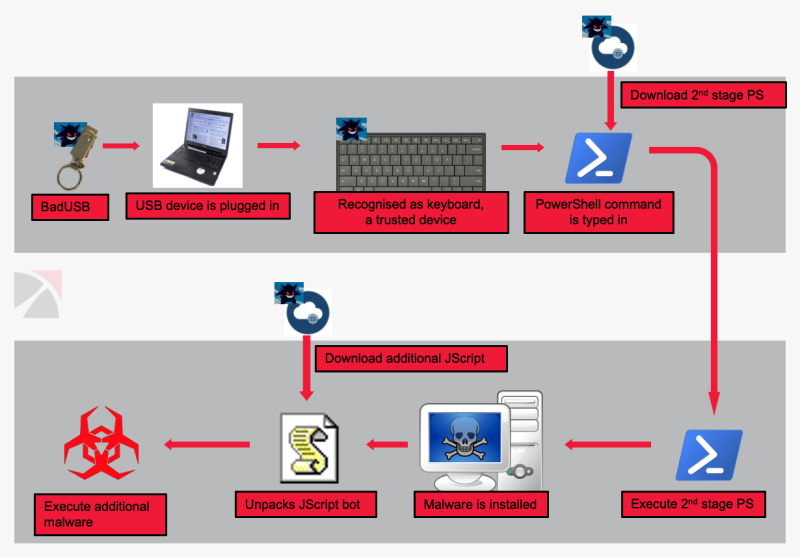
USB HID Attacks. USB HID devices are the way we interact… | by evildaemond | Heck the Packet | Medium

PDF) Spyduino: Arduino as a HID exploiting the BadUSB vulnerability | Vagelis Karystinos - Academia.edu

Ben S on Twitter: "Its compatible with any regular keyboard. Connects to a PC and looks like a regular HID keyboard. It uses man-in-the-middle attack and decodes the keyboards button presses from the real keyboard, then toggles caps lock on and off after ...

HID Attack. The external device can inject input events. The malicious... | Download Scientific Diagram